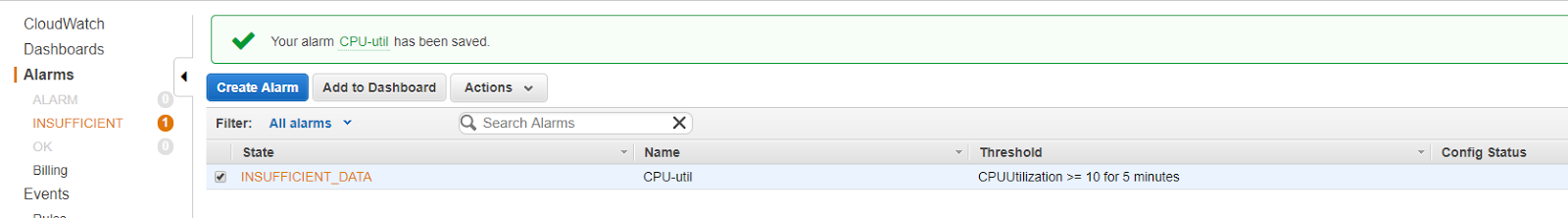
In this article I'll demonstrate the setup of a MySQL RDS instance in the AWS infrastructure. RDS is the category of relational database offerings from AWS which includes MySQL, Oracle PostgreSQL etc. It provides a cost efficient and flexible storage capacity solution to meet industry standard relational database needs.
Free tier use is available for all RDS options except Aurora. Both on demand and reserved instance purchasing options are available and the customers are charged based on the following metrics:
- Choice of database engine
- Database instance class (Similar to EC2 instance classes)
- Storage used
- Data transfer in/out of the instance
RDS instance provisioning:
From the AWS services view select RDS from the Database section.
Before we create our instance we need to create a DB subnet group. This will basically consist of two or more subnets from two or more availability zones to be used by RDS to assign an IP address to the DB instance we create.
I have created a DB subnet group for my instance as shown below:
With that task complete, click on the instances section under the RDS dashboard.
Now we need to click on launch DB instance. Once we do that we'll be presented with the below screen:
I've selected MySQL as the database engine for my DB instance.
After that we need to specify the intended use for the instance.
I won't get into the details of describing multi-AZ deployment and proviosned IOPS but I do feel the need to mention them in brief.
> A mult-AZ deployment will create a standby replica of our DB instance. The replica is invisible to us the users/customers. The benifit here is that all maintenance tasks like backups, snapshots and updates will be carried out on the standby replica. This is accomplished by AWS automatcially switching the DNS records of the primary and standby DBs on an as needed basis.
> Provioned IOPS helps us to increase the IO capacity of the DB instance by reserving a portion of the compute power of the underlying OS/virtual machine for IO operations only.
I've selected dev/test since I'll be using free tier. Make the approprate selection and click on next step.
Now, the following screen shown below we specify our DB details.
I've check marked the option to show me free tier configurations only.
Here we select the DB instance class, storage type, amount of storage to allocate, instance name and it's credentials. Once you've filled in these settings click next.
Now we are presented with the configure advanced settings screen.
Here we'll be supplying the VPC and the DB subnet group we created earlier to serve as the network prerequisites for the DB instance. An important point to note here is that I've set the instance to be publically available. This means that AWS will assign this instance an elastic IP via which it'll be accessbile over the internet.
I've also opted to create a new security groups because none of the existing security groups had port 3306 allowed which is required by MySQL.
This was the final step in the instance deployment process and now our DB instance will be deployed successfully.
Click on 'view your DB instances' to view the status of the instance.
This wil bring us to the instances section of the RDS dashboard.
The status of the DB is being shown as backing up which is actually a nice feature of RDS in that it takes a backup of the DB instance as soon as it's created so that we can do a somewaht 'restore factory settings' if we need to.
The instance creation takes upto 15 minutes to complete.
The endpoint is the DB hostname:port number combination that end users/applications will use to connect to the DB.
After waiting for a while I could finally see the status of the DB instance changed to available.
Now under instance actions, I'll click on instance details to get more information about the instance.
Now since the DB is up and running let's check to see if we are able to connect to it.
For this I've installed MySQL client on a CentOS 7 machine and will try to connect to the DB using the admin user that I had created during the instance configuration process.
As you can observe I was able to connect successfully to the DB instance and the database name I specified during the instance configuration has been created.
I hope this has been an informaive article for you and I thank you for reading.